Malvertisements are malicious advertisements distributed in the same way as legitimate online advertisements. It is one of the common practices to use spread malware. Cybercriminals use the advertising strategy by pretending as legitimate campaigns. Those malvertisements will either attempt to download malware directly onto visitor’s systems/devices or redirect visitors to websites meant to spread ransomware, viruses, or other malicious programs. The process of creating malvertisements and spreading malware is called malvertising. Malvertising is a favoured medium for criminal behaviour as it takes advantage of consumer trust in both companies running campaigns and advertising networks.
Ad networks are responsible for distributing real and fraudulent advertisements. The reliability of a website does not necessarily determine and has also been irrelevant to some extent to whether or not it will contain malvertisements. But saying that at the same time is the best place to be not infected with malvertisements. Recent examples have proven that even the most well-known, legitimate sites can distribute malvertisements unknowingly. In recent years, reputed sites such as Forbes, The New York Times Online, London Stock Exchange, Spotify, etc have all been negatively impacted by malvertising campaigns that infected visitors with malware.
People, in general, are confused between malvertisements and Adwares as they both deal with affecting online advertisements. Adwares are a program running on a victim or user’s system which is packaged with other legitimate softwares. Adware displays unwanted advertising, redirects search requests to advertising websites, and mines data about the user to help target or serve advertisements.
Key differences between malvertisements and adwares are:
1. Malvertisements involve deploying or injecting malicious code on a publisher’s web page. The targeted audience of malvertisements are not individual or selected users whereas Adware, however, is only used to target individual users.
2. Malvertisements are only dangerous and affect users that view the infected webpage or website whereas adwares once gets installed keeps on operating on the user’s computer.
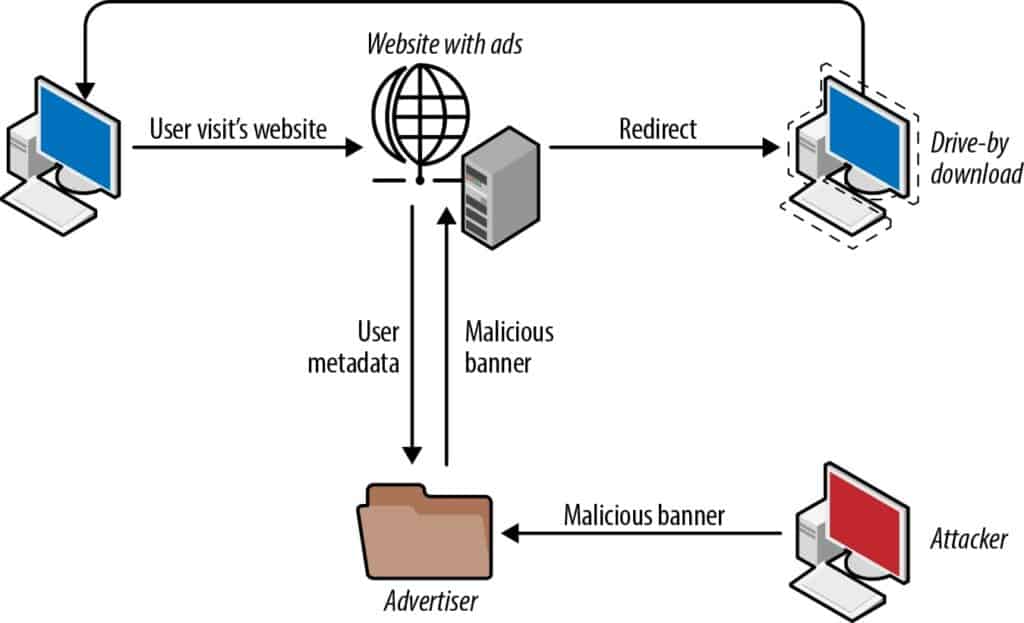
Malvertisements are distributed via the same methods as normal online advertisements. Infected graphic files are submitted to a legitimate advertisement network with hopes that the advertiser won’t be able to differentiate between trustworthy ads and harmful ones. Advertisements generally attract and encourage viewers to click. When approved by the advertisers these malicious advertisements are added or distributed on legitimate sites. In some cases, cybercriminals will even re-register expired, but previously legitimate, domains to disguise themselves as trustworthy domains. Criminals can use redirects to send clickers to a malicious site, and users remain ignorant because they expect redirects when clicking on an ad. While on the malicious website, code will run in the background which will attempt to download malware onto the device. This unintentional download of a virus or malicious code is known as a drive-by download. Malvertisements often use drive-by attacks to download ransomware onto targeted computers. Advanced forms of malvertisements can even install malware on visitor’s devices directly from the legitimate website that is displaying the ad and without any interaction from visitors.
Attackers or people with malicious intent use several delivery mechanisms to insert their malicious codes into advertisements.
1. Malwares in Advertisements calls: When a website shows a page featuring an ad, the ad exchange delivers advertisements to the user through a variety of third parties. An attacker can compromise one of these third-party servers, who can attach malicious code to the ad payload.
2. Post-click malware injection: Users who click on an ad are typically redirected between multiple URLs, ending with the ad landing page. If any of the URLs along this delivery path are compromised by an attacker, they may execute malicious code.
3. Malware in Text or Banner Advertisements: Malware may be found in a banner ad or text message. For instance, an ad can be delivered in HTML5 as a combination of images and JavaScript which may contain malicious code.
4. Malware within a pixel of an image: The pixels are embedded with codes in an advertisement call. A legitimate pixel sends data to the server for tracking purposes. If an attacker intercepts a pixel’s delivery path, it can send a response, containing malicious code, to the user’s browser.
5. Malware within the video: Video players don’t protect against malware. Examples can be videos based on flash or specific video formats such as VAST. Video format VAST contains pixels from third parties, which could contain malicious code. Videos based on flash can inject an Iframe into the page, which downloads malware, even without having the user click on the video. Flash files might also load a pre-roll banner and attackers can inject malicious code into the pre-roll banner, and it can run even without the user clicking on the video.
Common malvertisements generally need user interaction in order for the malwares to be downloaded in a victim’s system or infect the victim/user’s system. User interaction can be victims clicking on an unsafe malicious advertisement. Following attacks or things that might happen on users viewing or interacting with malvertisements:
1. Download or installation of malwares on the computer or systems viewing those malicious advertisements.
2. Redirect the user or victim to a malicious site.
Some advanced malvertisements can affect or cause harm to a user without user interaction. Malvertising might perform the following attacks on users viewing the malvertisements without clicking it:
1. A “drive-by download” — installation of malware or adware on the computer of a user viewing the ad. This type of attack is usually made possible due to browser vulnerabilities.
2. Forced redirect of the browser to a malicious site.
3. Displaying unwanted advertising, malicious content, or pop-ups, beyond the ads legitimately displayed by the ad network. This is done by executing Javascript.